Throughout my research into cloud security, the topic of identity management is always present. In fact, many in the industry feel that when it comes to securing the cloud, identity is the new perimeter. The challenge here is that most users require access to many different cloud-based applications to perform their job functions, and managing all those usernames and passwords can be a pain. As a result, passwords are written down on sticky notes placed under keyboards, hidden in unlocked desk drawers, or even applied directly to desktop monitors.
While poor password management may seem like a familiar challenge for veterans of the IT industry, the problem has undoubtedly worsened with the growing enterprise adoption of SaaS applications. In an effort to make the login process easier and more secure (although the question of increased security is still up for debate), federated identity frameworks such as Open Authentication (OAuth), Security Assertion Markup Language (SAML), and OpenID Connect were created. For the purposes of this blog, we’ll focus on OAuth.
What is OAuth, and why target it?
OAuth is not an authentication protocol, though it’s often confused for one. It is a web-based authorization framework that provides delegated access to applications. This method of delegating access is most often associated with consumer-focused websites that permit login with preexisting Google, Facebook, or Twitter accounts. However, OAuth adoption is rising among enterprises, thanks to increased use of cloud-based productivity applications and services (such as those offered by Microsoft and Google).
So what exactly does “delegated access” mean? Simply put, OAuth enables users to grant applications access to their accounts and data without sharing their credentials. Once a user authorizes the requested access, an access token is created and shared with the requesting application. This process allows the application to take advantage of the assigned permissions until the token is manually revoked. While it is extremely convenient, OAuth usage presents a serious threat to the security of enterprise cloud deployments. To illustrate my point, here’s an example:
You arrive at work and start your day by checking your email. Today you’ve received an email from Fred in HR, inviting you to view a document he’s shared using Google Drive. When you click the link to access the file, a browser opens that requests authorization for Google Drive to “Manage all your files” and “Read, send or delete messages on your behalf.” Without paying too much attention, you click “Allow.”
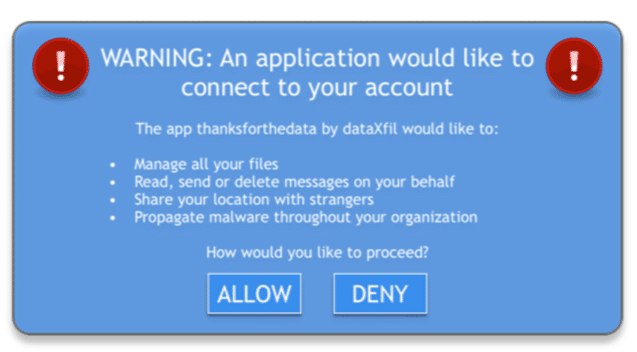
Unfortunately, Fred isn’t really Fred. Fred is actually Dimitri, a hacker who has just manipulated you into utilizing OAuth, which provides him with unrestricted access to your Google account. Unbeknownst to you, Dimitri is now able to leverage your Google account to initiate a similar phishing attack on other users, exfiltrate data you’ve stored in Google Drive, or upload and propagate malware.
As you can see, it’s the simplicity of OAuth that makes it scary. Let’s face it—whether we’re on our laptops or we’ve just downloaded a new app to our mobile devices, few of us actually take the time to read every pop-up or landing page we’re redirected to. When you couple the widespread distribution of OAuth with the click-happy nature of users, you end up with an attractive vector for hackers launching phishing campaigns to exploit.
How can you combat OAuth attacks?
Start by educating your users. Bring awareness to the potentially devastating effects of allowing an application to act on their behalf. Users should know that if their account is compromised, simply changing the password won’t help. Teach them how to manually go into their account settings and revoke the unwanted access tokens.
Next, you’ll need to gain visibility into OAuth usage across your entire organization. Since OAuth is predominately utilized by cloud-based applications, traditional network security and endpoint protection products won’t help much. Security administrators will need to deploy products that facilitate the governance of the enterprise’s cloud-based application usage, such as a cloud access security broker (CASB).
Many CASB products can be connected to compatible cloud service APIs and provide visibility into and control of the application. Security administrators can leverage these products to discover anomalous application-to-application activity and enforce policy that blocks any excessive permission requests.
Visit the NSS Labs Research Library to view and download group test reports, analyst briefs and other valuable resources that help enterprises to make informed cybersecurity purchasing decisions.
John Whetstone leads research focused on cloud and data center security technologies at NSS Labs. He has worked with enterprise cybersecurity products for more than 15 years and has held roles in the IT security industry that include administration, analysis, architecture, and engineering.
