Next Generation Firewall (NGFW)
Next Generation Firewall (NGFW)
TECHNOLOGY DESCRIPTION
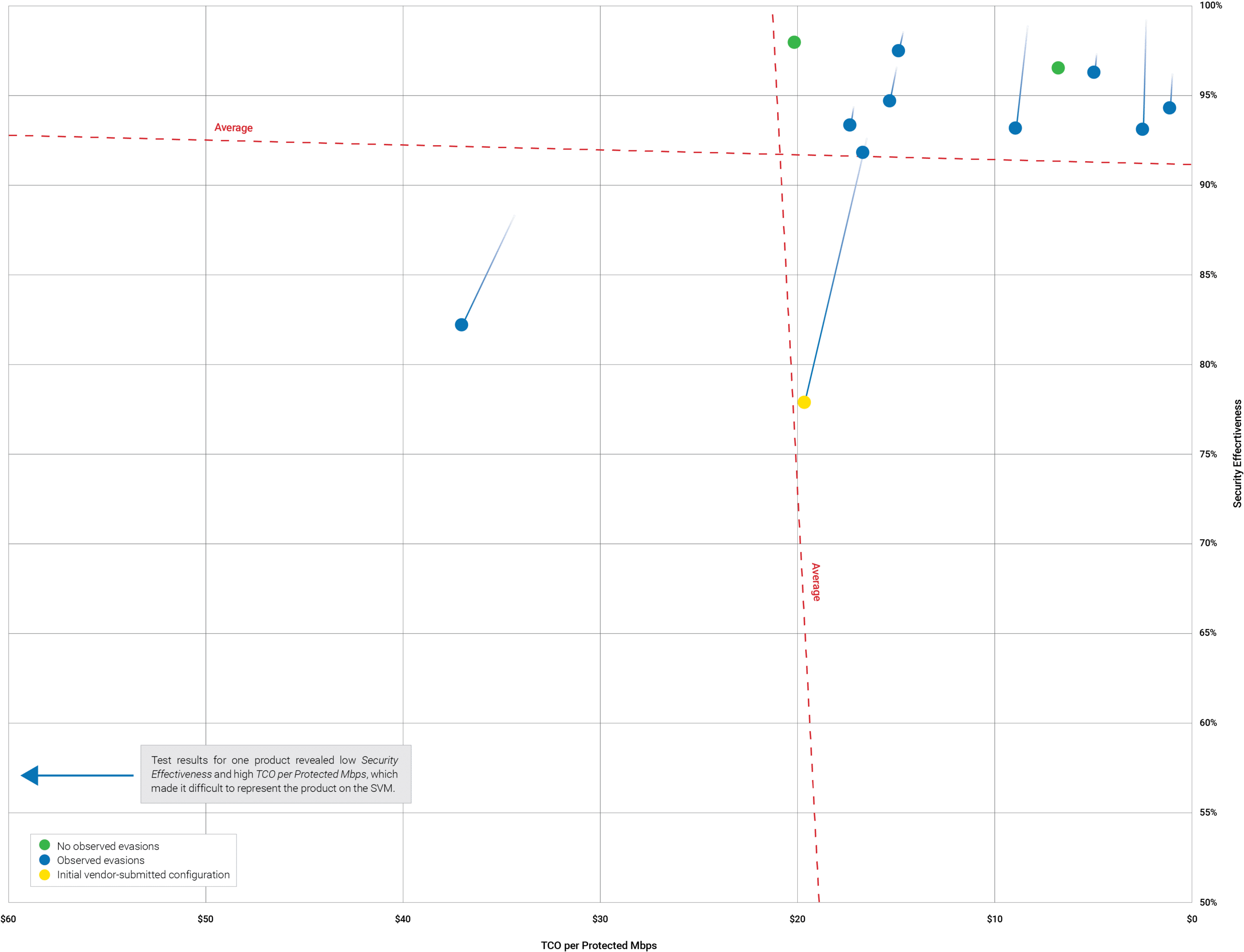
In the ninth NSS Labs NGFW Group Test, 12 of the industry’s leading NGFW products were tested to compare capabilities across multiple use cases. Products were assessed for security effectiveness, total cost of ownership (TCO), and performance.
Firewalls are the most widely deployed network security devices. Enterprises expect modern firewalls (NGFWs) to prevent exploits and malware from infecting critical systems.
TECHNOLOGY DESCRIPTION
The next generation firewall (NGFW) is the first line of defense against today’s threats, and as such, is a critical component of any defense-in-depth strategy. The NGFW market is one of the largest and most mature in the cybersecurity industry. NGFW technologies have evolved from packet filtering and circuit-level gateways to application layer (proxy-based) and dynamic packet filtering firewalls that use port and protocol combinations to create and enforce access control policy between trusted and untrusted networks.
Traditional firewalls relied on common application ports to determine which applications were running and which attacks to watch for, but the NGFW can identify and allow, block, or limit applications regardless of the ports and protocols used. NGFWs are capable of performing deep packet inspection on all packets, on all ports, and over all protocols in order to determine which applications are running over which ports and thus secure them effectively.
The increased use of SSL/TLS in traffic traversing the modern network makes it necessary for an NGFW to be capable of decrypting content.
WHAT WE TESTED
NSS raised the bar this year by performing a significantly tougher test for security effectiveness, which exposed weaknesses not seen previously. Results showed that block rates for simple clear-text attacks remain strong; however, while known/published exploits were frequently blocked, test engineers were able to bypass protection in all devices with minor modifications to known and blocked exploits. In addition, only one of the 12 products tested properly blocked exploits that were obfuscated using complex evasions (HTML / JavaScript / VBScript).
KEY TAKEAWAYS
-
Enterprises expect when they purchase products that they will remain viable over multiple years.
-
While it is tempting to draw conclusions from one test, NSS recommends enterprises favor vendors that consistently engage and improve over time. When in doubt, an NSS analyst is available to answer questions.
-
Scripting evasions are challenging for NGFWs since they require real-time code analysis in order to determine whether a function is legitimate or obfuscating an attack.
-
Vendor claims to protect vulnerabilities (regardless of the exploit specifics) are largely dependent on the nature of the vulnerability and whether it lends itself to such protection. Test results found all products had room for improvement when confronted with unknown variants of known exploits.
-
Research indicates that over 70% of Internet traffic is encrypted using TLS/SSL. NSS recommends measuring the performance of devices both with and without TLS/SSL enabled. Failure to do so could result in unexpected performance bottlenecks.
PRODUCTS EVALUATED:
- Barracuda Networks CloudGen Firewall F800.CCE v7.2.3
- Check Point Software Technologies 6500 Security Gateway R80.20
- Cisco Firepower 4110 Security Appliance V6.3.0.2
- Forcepoint 2105 NGFW v6.3.11
- Fortinet FortiGate 500E v6.0.4 build 0231
- Huawei USG6620E v600R006C00SPC310
- Juniper Networks SRX4600 V18.4X3.3
- Palo Alto Networks PA-5220 PAN-OS 8.1.6-h2
- Sophos XG 750 Firewall SFOS v17.5
- SonicWall NSa 4650 SonicOS v6.5
- Versa Networks FlexVNF v16.1R2-S7
- WatchGuard Firebox M670 Firmware: 12.3 B589695 Ver-4.907
