BREACH PREVENTION SYSTEM (BPS)
BREACH PREVENTION SYSTEM (BPS)
TECHNOLOGY DESCRIPTION
Breach Prevention Systems (BPS) are solutions suites that involve the integration of different products such as endpoint, network, sandbox, cloud, and other protections.
Vendors have been claiming for years that if enterprises purchase their entire suite, they will see better results. Enterprises asked us if this was true, as many perform technology proofs-of-concept (PoCs), but few have the resources to test a multilayer defense with so many integrated protections.
TECHNOLOGY DESCRIPTION
Breach Prevention Systems (BPS) are solutions suites that involve the integration of different products such as endpoint, network, sandbox, cloud, and other protections.
Vendors have been claiming for years that if enterprises purchase their entire suite, they will see better results. Enterprises asked us if this was true, as many perform technology proofs-of-concept (PoCs), but few have the resources to test a multilayer defense with so many integrated protections.
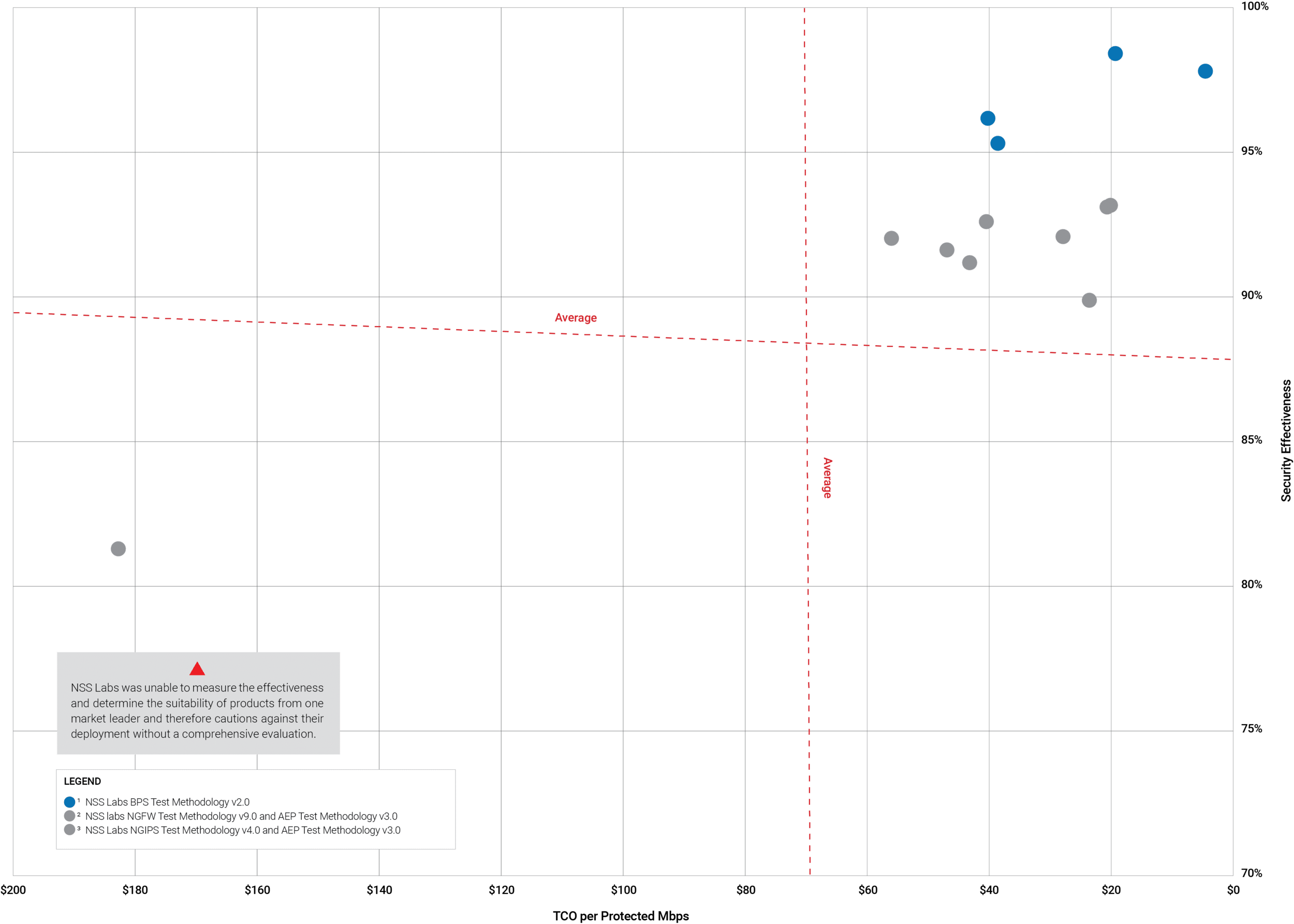
WHAT WE TESTED
2019 is the first time we have published a comparison of technology suites. This comparison is the outcome of testing Next Generation Firewalls, Next Generation Intrusion Prevention Systems, Breach Detection Systems, and Advanced Endpoint Protection products.
All tests permitted the use of cloud capabilities such as reputation systems, sandboxing, emulation, machine learning, and so on.
WHAT WE FOUND
- Some vendors are better at developing integrated/coordinated technical solutions than others. (Always validate marketing claims!)
-
Many organizations purchase endpoint, network, cloud, and forensic security technologies at different times. This makes it harder to select coordinated security solutions.
-
Few vendors provide good protection from multiple attack vectors across all defensive layers.
-
Vendors still find evasions challenging, but agile development processes help with rapid remediation.
-
Vendor claims to protect vulnerabilities are largely dependent on whether the vulnerability allows such protection. We found all products need improvement when dealing with unknown variants of known exploits.
PRODUCTS EVALUATED:
-
Fortinet FortiGate 500E v6.0.3 + FortiClient v6.0.3.6219 + FortiSandbox v3.0.2 (AWS BYOL)
- Fortinet FortiGate 500E v6.0.4 build 0231 & Fortinet FortiClient v6.0.3
- Fortinet FortiGate 500E v5.6.4GA build 7892 & Fortinet FortiClient v6.0.3
- Fortinet FortiGate 3000D v5.6.4GA build 7892 & Fortinet FortiClient v6.0.3
- Palo Alto Networks PA-5220 PAN-OS 8.1.2 + Traps v5.0.5.2072
- Palo Alto Networks PA-5220 PAN-OS 8.1.6-h2 & Palo Alto Networks Traps 5.0.6.6513
- Palo Alto Networks PA-5220 PAN-OS 8.1.2 & Palo Alto Networks Traps 5.0.6.651
- Sophos XG 750 Firewall SFOS v17.5 & Sophos Intercept X Advanced v2.0.10
- Trend Micro TippingPoint 8200TX Appliance v5.1.0.49751 + Deep Discovery Analyzer v6.1.0.114 + OfficeScan v12.0.5024
- Trend Micro TippingPoint 8400TX v5.1.0.4965 & Trend Micro Smart Protection for Endpoints v12.0.5024
- Vendor A (contact NSS Labs for more information)

