OUR APPROACH TO SECURING THE ENTERPRISE HAS CHANGED, AND BREACH DETECTION TECHNOLOGY HAS BEEN LARGELY INSTRUMENTAL IN THIS PROCESS. THIS REPORT FROM NSS LABS IS THE FIRST IN A THREE-PART SERIES ON THE IMPACT OF THE BREACH DETECTION SYSTEM (BDS).
One of the newest security technologies on the market today, breach detection is a technology that that has undergone rapid change in a short amount of time. Vendor innovation has been extraordinary and customer interest has been intense. In light of current security events, security practitioners have had to confront several new realities:
- The definition of “breach” must be expanded beyond “inbound” (malware has circumvented traditional defenses) to recognize that a breach also has an “outbound” component (data has been exfiltrated)
- There is a need for a security technology that goes beyond signatures (i.e., information that is supplied by vendors – and according to their schedule) and provides custom detection capabilities (i.e., local detonation chambers).
Today’s security devices are required to “detect the invisible” – unknown malware and their indicators of compromise (IoC). A breach detection system can do this and more, and all on a single platform.
The NSS 2014 Market Intelligence Brief on breach detection systems offers the following definition:
“Through constant analysis of suspicious code and identification of communications with malicious hosts, breach detection solutions (BDS) are capable of providing enhanced detection of advanced malware, zero-day and targeted attacks that could bypass defenses such as next generation firewalls (NGFW), intrusion prevention systems (IPS), intrusion detection systems (IDS), antivirus/endpoint protection (including host IPS), and secure web gateways.”
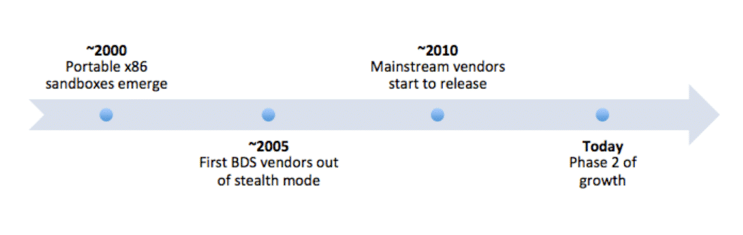
The breach detection market has a history that dates back almost 15 years. Breach detection systems first surfaced circa 2005, and by 2010 the technology had begun to gain momentum. Today, the BDS market is exploding; most traditional antivirus vendors have released some version of a breach detection product, some as recently as early 2014.
EVOLUTION OF BREACH DETECTION SYSTEMS
Breach detection systems have become popular because they can detect malware that would otherwise go undetected, i.e., the malware cannot be detected using traditional means.
Early breach detection focused on identifying inbound malware; today, many BDS incorporate outbound elements during analysis, such as data exfiltration and other indicators of compromise, which provide security teams with critical forensic information. While the inbound phase of a breach is concerning, it is the outbound phase (attempted data exfiltration) that is most important, since it represents the last opportunity to detect the threat before irreversible damage, i.e., data loss, occurs.
Dynamic investigation of unknown threats is a core requirement of a beach detection system. To this end, most BDS use sandbox technology, or malware “detonation chambers.” Typically, sandboxes are virtual machines (VMs); bare metal sandboxes can also be utilized, but they are not common (by using VMs, multiple sandboxes can be installed on a single appliance and these sandboxes can be quickly re-created). Sandboxes are considered a baseline feature in today’s leading breach detection products. They are, however, computationally expensive, and most vendors limit their use, instead relying on other malware detection techniques.
The ability of a breach detection system to “detect the invisible” is particularly important because of the many zero-day attacks that are tailored for specific organizations. Such attacks are concerning because they represent a clear desire for data exfiltration. When data is compromised, the impact to the business, or even the economy, is considerable. The 2014 Cost of Data Breach Study by the Ponemon Institute states: “The average cost for each lost or stolen record containing sensitive and confidential information increased from $188 to $201. The total average cost paid by organizations increased from $5.4 million to $5.9 million.”
Breach detection systems have become a compelling alternative to traditional security technologies that fail to detect breaches. Despite its complexity and cost, enterprises would be well served to review the technology closely.
NEXT UP: a discussion of the features in emerging and leading BDS; the expanding definition of BDS and how this technology fits into big data system analytics (BDSA), including security information and event management (SIEM) and continuous forensics analytics (CFA).
