With software as a service (SaaS) becoming an increasingly popular method of delivering software, more and more organizations are moving their IT and productivity applications to the cloud—and those organizations that have not moved their apps are dealing with shadow IT issues. Given this new environment, it would be beneficial for CIOs and CISOs to have security policy enforcement points (PEPs) in the cloud, cloud access security broker (CASB) provides PEPs to the enterprise.
A number of start-ups have used different approaches to provide visibility, control, data security, and compliance for cloud applications. Initially, CASBs were focused on visibility and compliance; however, over the last couple of years, other important functionalities have been added, e.g., threat protection, contextual access policies, more granular control on DLP and DRM, agentless mobile device security, encryption for new apps, dynamic policies, threat protection, and machine learning. CASBs provide secure access for any user, using any device, accessing any document, from anywhere, at any time, and to any CSP applications. CASBs also deliver a unified view across different SaaS applications by supporting visibility into the who (user), what (activity, SaaS, and resource), when (time), where (location), and which (device) of cloud services usage.
BRINGING COMMON ELEMENTS FROM EXISTING SECURITY CATEGORIES UNDER ONE UMBRELLA
CASBs have inherited some of the best functionalities from existing security technologies such as next generation firewall (NGFW), secure web gateway (SWG), cloud encryption gateway, antivirus, threat protection, and security information and event management (SIEM).
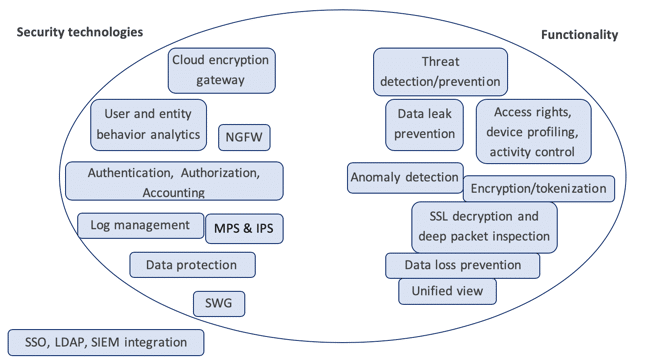
CASBs incorporate functionality from the following technologies:
- NGFW: authentication, authorization, credential mapping, device profiling, logging, alerts, access rights, and more granular control over thousands of apps
- Cloud encryption gateway: encryption and tokenization
- Malware prevention system (MPS)/intrusion prevention system: threat detection and prevention leveraging detection, analysis, and response (e.g., containment, blocking, remediation, repair)
- SIEM: threat protection, centralized view, and user and entity behavior analysis
- SWG: regulation and compliance on web traffic, malware detection/prevention, and SSL
DEPLOYMENT MODE AND ARCHITECTURE
The most common deployments for CASBs are forward proxy, reverse proxy, and API scan mode that is not an inline proxy.
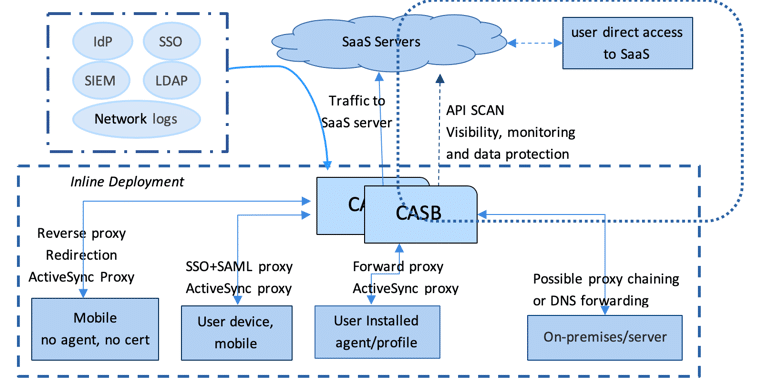
CASBs offer way too many moving parts: forward proxy, reverse proxy, active sync proxy, cloud discovery proxy, enterprise integration, SSOs, SIEM and log integration, encryption key management services, and cloud encryption gateways, among other complexities. As a result, they have become bulky.
Networks are already overcrowded with control points, such as distributed denial-of-service (DDoS), server load balancing (SLB), NGFW, web application firewall (WAF), key management servers, intrusion prevention systems (IPS), and SWGs. Adding one more proxy (CASB) that requires changing the existing setup makes the network administrator’s job more complicated. It would be better to consolidate all of these into one solution.
THE BOTTOM LINE
CASBs should be evaluated with the expectation that they most likely will not remain stand-alone products/services. Some vendors will be acquired by larger companies that will merge the CASB features into their existing NGFWs/SWGs. For example, Blue Coat, Microsoft, and Palo Alto Networks have acquired Elastica, Adallom and CirroSecure (Aperture). Most recently, Cisco has announced its intention to acquire CloudLock for its API-based model and for its visibility into IaaS and PaaS. Other vendors will add more NGFW, SWG, and WAF functionality to create a complete security ecosystem that will give coverage far beyond http/https.
While CASBs today are heavily focused on providing functionality for SaaS, we expect them to move horizontally and improve their support for platform as a service (PaaS) and infrastructure as a service (IaaS).
Moving forward, CASB vendors must refine and simplify their approach and find a smart way to include PaaS without overcomplicating things. Small start-ups should take care not to overload themselves with features and builds for every customer, and they should add value that their bigger competitors (e.g., Microsoft, Salesforce, Palo Alto Networks, and Blue Coat) can’t provide.
