First patented in 1994 by Check Point Software, stateful firewalls are an evolution of the packet filtering firewall. Stateful firewalls were a game changer because they introduced state tables, which permit a firewall to store the status (or state) of each network connection. This information enables stateful firewalls to examine session information (layer 4) as well as inspect each packet’s source and destination information. The session information is compared to existing connections recorded in its state table. If an established connection exists, traffic is allowed to pass through unimpeded; if not, the firewall will perform inspection at both layer 3 and layer 4 prior to making the decision to allow or deny. This process drastically increases the efficiency with which these second-generation firewalls route traffic.
Stateful firewalls are a bit like the doorman at a club. To get into the club you’re required to show him your ID; after he inspects your ID and verifies that you are of legal age to enter, he lets you in. If you need to go out to your car and grab something, he remembers who you are and lets you back in without a hassle.
Much of the data in our 2017 US Enterprise Architecture study has been eye-opening, but the data from our stateful firewall study has been particularly interesting.
Our survey results showed that 94.6% of respondents from US enterprises indicated that their organization deploys a stateful firewall, whereas 80.5% of respondents have indicated that their organization deploys a next-generation firewall (NGFW). Interestingly enough, 80.2% of respondents who deploy any form of firewall indicated having both stateful and NGFWs deployed within their environment. Additionally, stateful firewall deployments have little variance across horizontals.
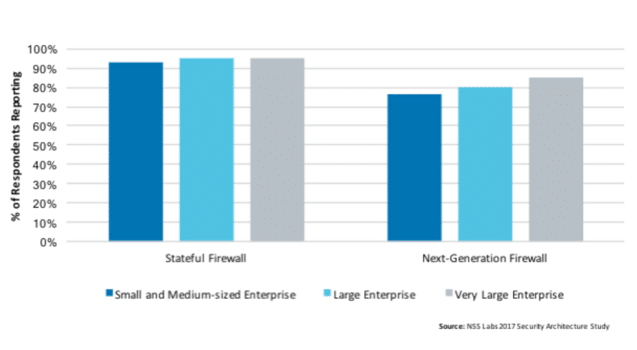
Did you find this data surprising? It was somewhat surprising to me. I anticipated that survey results would show stateful firewall deployments to be on the decline by now and that NGFW deployments to be dominating the enterprise firewall landscape. After all, NGFWs are nearly a decade old themselves, and clearly have been designed—and marketed—to be an evolution of perimeter defense. Perhaps this is because enterprises aren’t fully utilizing the next-gen features of these devices.
Stateful firewalls are most often managed by network operations teams (43.1%), whereas their next-gen brethren are most often managed by security operations teams (42.7%). This makes sense when you take into consideration the addition of features such as intrusion prevention, anti-malware, application control, and in some cases, sandbox integration in NGFW products.
Will the purpose-built stateful firewall continue to be the most commonly deployed firewall for another two decades? Probably not. As networking and security technologies continue to converge, based on the requirements of the enterprise, Old Stateful’s reign will likely come to the end. But that’s a topic for another time.
NSS Labs has released a series of Intelligence Briefs that focus on security controls in the US enterprise, one of which is focused on stateful firewall products. The series will report on security product usage as reported by 510 information security professionals representing 50 US industries. This paper is available in our research library.
