DEPLOYMENT AND HTTP/2
Web application firewalls (WAFs) are a growing segment of the security market. WAFs employ a wide range of functions to work in conjunction with perimeter firewalls and intrusion prevention system (IPS) technologies and provide protection specifically for web applications. WAFs can be deployed as stand-alone appliances, virtual appliances, or self-contained software designed specifically to secure web-based traffic.
Key Findings:
- Most WAFs are deployed inline (41%), via reverse proxy (30%), or as a cloud resource (20%)
- 61% of respondents rely on learning mode to initially tune their WAFs
- 71% of respondents currently monitor HTTP/2 traffic
- 50% of respondents report organizational changes to their roadmap as a result of increased HTTP/2 traffic
In November 2016, NSS Labs conducted an independent study to gain insight into enterprise WAF deployment, integration, labor and maintenance, and perceived value. We surveyed 128 cybersecurity officers (n=128) from Global 2000 companies headquartered in North America that actively deploy WAFs.
This blog will discuss WAF deployment and HTTP/2, while Part 2 will report our findings on WAF integration, labor and maintenance, and perceived value.
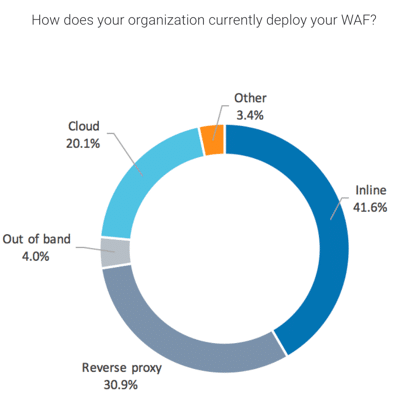
WAF Topology
WAFs have multiple form factors and implementation options. When asked how their organizations implement WAFs, most respondents (41.6%) chose inline deployment. The next most common answers were reverse proxy, cloud, and out of band (30.87%, 20.13%, and 4.03%, respectively). A few respondents (3.36%) reported alternate deployments (e.g., CA API Gateway, IIS).
Learning Mode
Web-accessible applications have myriad attack vectors, including SQL injections, parameter tampering, forceful browsing, cross-site scripting, buffer overflows, man-in-the-middle attacks, session hijacking, and denial-of-service attacks. Considering the number and variety of these threats, as well as the importance of accurate tuning (e.g., the configuration of suitable whitelists), WAFs have long been viewed as challenging devices to maintain.
We asked participants if they relied on the learning mode of their WAFs to simplify these efforts. Of our respondents, 61% reported that their organizations rely on this function. Some enterprises may not use this function due to the risk of error during the learning period, concern for poor performance, lack of skilled technicians, or lack of security architect resources.
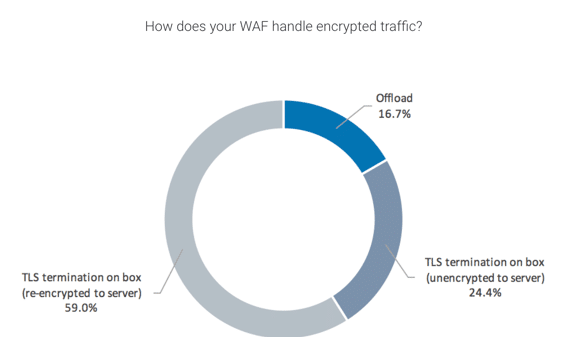
Encrypted Traffic
As previously stated in an NSS brief on encrypted technology, we predict that 75% of all web traffic will be encrypted by 2019. For this reason, survey participants were asked how their WAFs handle encrypted traffic. Results indicate that 58.97% of respondents use their WAFs via TLS termination on box (re-encrypted to server), 24.36% use their WAFs via TLS termination on box (unencrypted to server), and 16.67% offload their encrypted traffic.
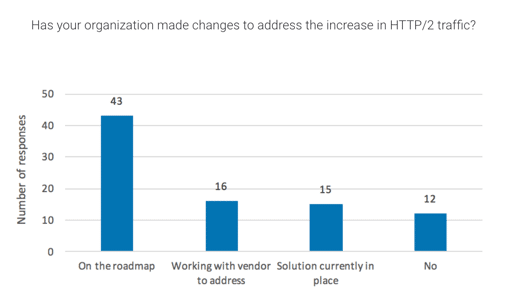
HTTP/2
Along with the rise in encrypted traffic, there has been a marked increase in HTTP/2 traffic in the past year. Using Amazon’s Alexa website popularity rankings, W3Techs has observed in an ongoing survey that as of January 31, 2017, HTTP/2 traffic is being used by 11.4% of all websites—more than twice the number of websites that used it in January 2016. When we asked enterprise cybersecurity officers if their organizations had made changes to address the rise in HTTP/2 traffic, we found that 50% of respondents have plans for organizational changes on the roadmap, 18.6% are currently working with vendors to address the increase, 17.4% currently have solutions currently in place, and 13.9% are not planning to make changes.
1 Usage of HTTP/2 for Websites, W3Techs, Historical Trend, accessed 19 Jan 2017, at https://w3techs.com/technologies/details/ce-http2/all/al
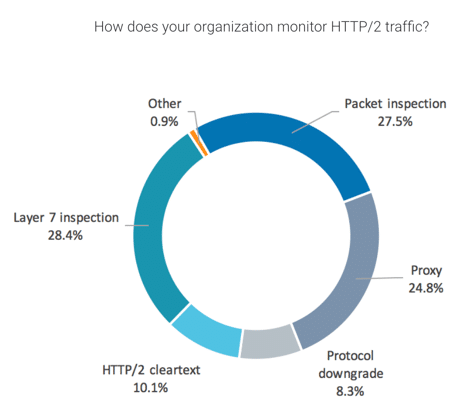
When asked if their organizations currently monitor HTTP/2 traffic, 71% of respondents reported that they do, with most of the monitoring being done through Layer 7 inspection, packet inspection, or by proxy. Other participants reported monitoring HTTP/2 through cleartext, protocol downgrade, or other methods.
In Part 2 of this blog, we report our findings on WAF integration, labor and maintenance, and perceived value.
