Phishing scams exploit human weakness to gain access to sensitive information, and they are among the most common cyberattacks that individuals and businesses must protect against in the struggle to keep their information secure. Cybercriminals leverage different mediums, including email, text, and social networks to impersonate legitimate communications and deceive users into giving up sensitive information such as credit card details, login credentials, social security numbers, and secret questions and their answers. This personal information is used to leverage future attacks and bypass automation identification such as captchas.
Phishing continues to pose serious security challenges for typical users and the number of these attacks is increasing. They are attractive to cybercriminals because they are not only effective but also scalable. It is relatively easy to target hundreds of thousands of users with one attack; attacks are often platform-agnostic; they are relatively simple to carry out, and they can be perpetrated over and over again to gather information, which when combined, can be used as a powerful profiling tool.
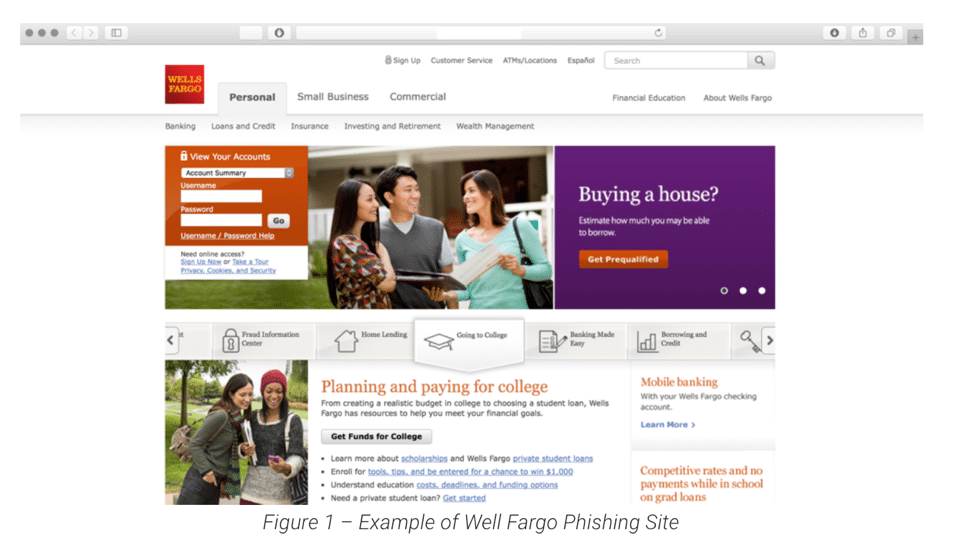
Websites have a vested interest in making sure their systems work for all browsers and operating systems. The phishing page mirrors websites to mine sensitive information, and it works on Windows, Mac OSX, Linux, mobile devices, and importantly for this assessment—also on Chromebooks. Phishing differs from exploit kit activity and is often more attractive for cybercriminals because exploits are very rarely cross-platform, and even within the same platform, they are typically architecture-specific.
The information that criminals gather from phishing campaigns is sold on the underground market where it is used to perpetrate further crimes and attacks. Some phishing attacks are precursors to larger targeted attacks and are used to gather the information necessary to plausibly impersonate intended targets and their coworkers and friends.
[1] APWG: Phishing Activity Trends Report hxxp://docs.apwg.org/reports/apwg_trends_report_q4_2016.pdf
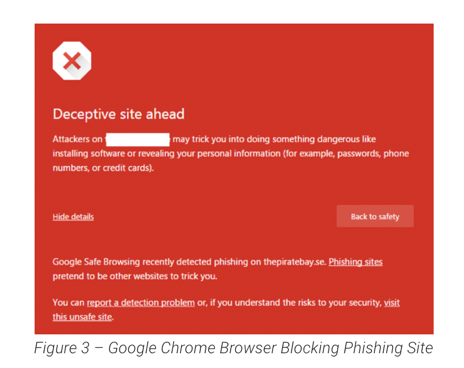
The growth of e-commerce has enabled threat actors to achieve their phishing objectives with relative ease, and leading browser vendors are constantly adding protection mechanisms to tackle these threats. Google Chrome leverages the Google Safe Browsing API to determine unsafe web resources, which when it was first created, was responsible for detecting phishing and drive-by download attacks but is now also responsible for determining which web resources are hosting malware.
Mozilla Firefox and Apple Safari also leverage the Safe browsing API to determine unsafe web content. Microsoft uses its SmartScreen filter to block phishing attacks in its Internet Explorer and Microsoft Edge browsers. The filter can be enabled in the browsers’ settings. SmartScreen filter has done a good job in blocking phishing sites as noted in a 2016 study by NSS.. NSS recommends that all users ensure they are using either the Safe Browsing API or the SmartScreen filter, regardless of which platform they are on. Visit the Google Chrome Help Center for instructions on how to check that you are using these capabilities, or if you are not, to learn how to enable them.
Because of a large number of requests from NSS clients in the education sector to evaluate Chromebooks, and because NSS has observed a rise in the number of Chromebooks deployed here, NSS recently chose to conduct a phishing test to measure the security efficacy of running Google Chrome on Windows vs. running Google Chrome on Chromebooks. Google Chrome version 57.0.2987 was tested on both the Windows platform and the Chromebooks platform. To provide a diversity of samples, NSS sourced phishing content from open-source threat intelligence feeds and from its partner feeds.
[2] NSS Labs Web Browser Security Comparative Report: Phishing Protection
https://nsslabs.com/research-advisory/library/endpoint-protection/web-browser-security/web-browser-security-comparative-report-phishing-protection/comparative-report-web-browser-security-phishing-protection/
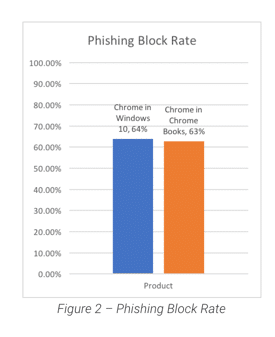
NSS observed near-identical performance from both Windows and Chromebooks. The minor difference in the test results is most likely due to factors such as different look-up response times, the frequency of local cache updates, and small deltas in test execution times.
In this test, Google Chrome blocked 64% of the phishing sites that were part of the sample set, down from the 84% it blocked during our testing in October 2016. This is not unexpected as attackers and defenders are continually jockeying for better positions and “penetration rates.” We believe that continuous testing would indicate a sinusoidal pattern as this jockeying takes place.
While browsers provide a valuable first line of defense to block the phishing sites, user education is still key to avoid compromise by phishing sites. NSS Labs recommends the following best practices:
- Verify the validity of emails and web pages by contacting the sender directly and typing in addresses manually. Never click on a link you have not verified.
- Never reveal account numbers and PIN numbers as part of an email response, and never enter credentials to a website that you arrived at through clicking a link in an email.
- Be suspicious if someone is unexpectedly asking for sensitive information such as credit card or Social Security numbers.
- Never provide a social security number online unless you are filing your taxes or applying for credit from a reputable website.
- Don’t reuse the same password across different websites and use a password manager to ensure strong passwords that are unique.
