Web application firewalls (WAFs) are network security controls that monitor, filter, and control web traffic between clients and web-based applications. Users are learning that even tested web protocols can deliver threats. A traditional firewall blocks or accepts traffic based on routing details (e.g., source, destination, protocol type); WAFs dig deeper, inspecting traffic all the way down to the application layer and providing protection against attacks such as zero-day exploitation, cross-site scripting (CSS), SQL injection, cross-site request forgery (CSRF, i.e., session hijacking) and buffer overflows.
Web applications are ubiquitous in today’s digitally connected world, and end users are accessing an increasing volume of content. While only a small portion of overall traffic may be malicious, the impact of even a single successful breach can be disastrous, and the need to scrub data moving into and out of web applications remains critical.
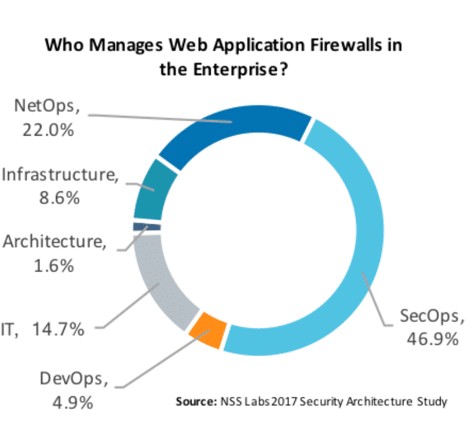
WAF ownership is divided primarily between security operations (46.9%), network operations (22.0%), and IT (14.7%) teams. In any enterprise, these teams must work together to orchestrate the installation, management, and tuning of the product in order to facilitate business continuity.
Are there alternatives to WAFs? Absolutely. Next generation firewalls (NGFWs) and next generation intrusion prevention systems (NGIPS) are just two examples of other application-layer firewalls. NSS Labs will continue to evaluate these technologies in order to help enterprise security teams understand which products best fit their environments.
NSS Labs will be releasing a series of Intelligence Briefs that focus on security controls in the US enterprise, one of which is focused on web application firewalls. The series will report on security product usage as reported by 510 information security professionals representing 50 US industries.
